Endoacustica offers, Exclusive Customer Service and free Training
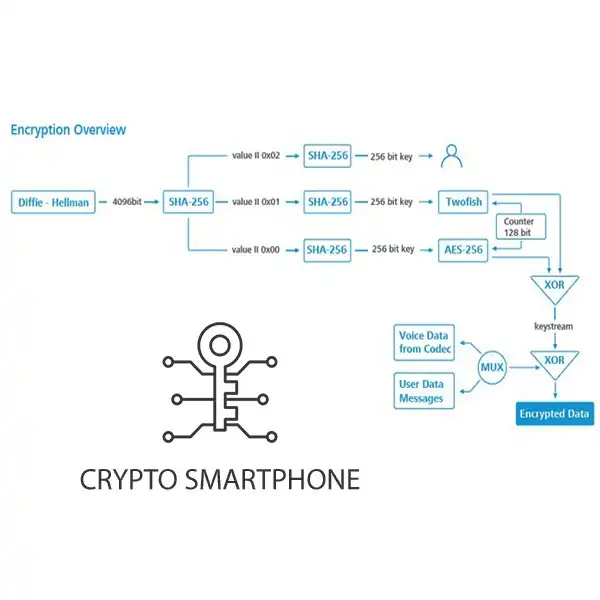
Encrypted mobile phone for secure calls
- Double military-grade encryption algorithmm
- AES256 encrypted calls and messages
- Anti-IMSI-Catcher security system
- Impenetrable and anti-chip-off hardware
- OS without backdoors
prod cod: CP-700

Free customer service:
 Technical and operational support
Technical and operational support
![]() Pre-Sale assistance
Pre-Sale assistance
 Dedicated consultation service
Dedicated consultation service
 After-Sales training and support
After-Sales training and support