Micro Video Recorders? It may be a bit too late for a Christmas present for a relative or a friend, but it’s never too late to make yourselves ready in case you have to take video footage on the go. How micro video recorders used for holidays? If during your
Category: Technology
Large technology research sector, in which various technical and scientific disciplines are involved, which studies the application and use of everything that can be functional to the solution of practical problems.
GSM encryption unveiled: is our privacy at risk?
GSM encryption? Many sites worldwide are reporting today the news about a young German hacker who published the algorithm used by GSM cellphone networks to encrypt their phone calls. It is a 64-bit encryption key called A5/1. How is GSM encryption unveiled? This encryption has been used for well over
GSM Bugs
GSM bugs are covert listening devices which, in order to transmit their intelligence, use the mobile phone network, thanks to a SIM card installed on them. Among the endless possibilities offered by the eavesdropping devices market, the usage of a GSM bugs has become more and more widespread, especially in
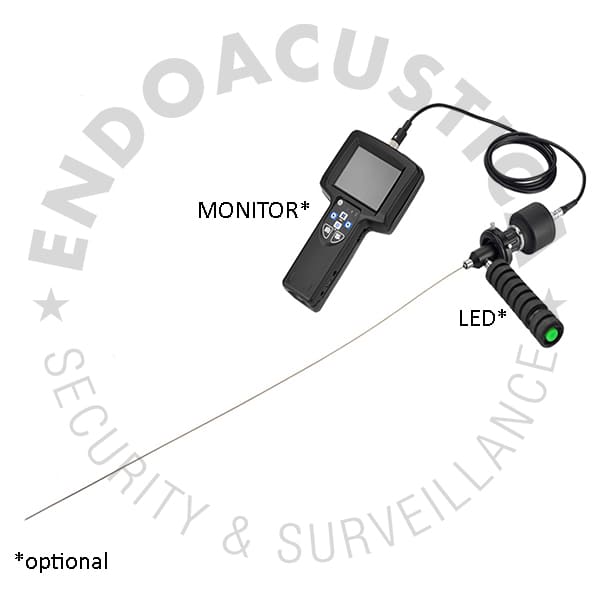
A flexible photo camera, to reach everywhere
Flexible Photo Camera? The Russian designer Art Lebedev is famous for his extravagant but useful concepts, such as for example Transparentius, a large screen mounted on the back of a transport truck and connected to a camera placed on the front, which allows car drivers behind the truck to see
Take Up Thy Stethoscope…. and Listen, in secret
Stethoscope? How many times did we find ourselves wishing we could listen to what our colleagues in the next room are saying, to find out what they really think about us? Or that we could spy on our annoying neighbor to expose his strange (or even illegal) habits? In many
New camouflage suits for the British Army
Camouflage suits? The BBC has reported yesterday that the infantry of Her British Majesty’s Army will be equipped, starting from the month of March 2010, with a new camouflage suit that will replace the one that has been used for more than 40 years without any change. The MTP (Multi
Target detection via GPS
Target Detection? The British manufacturer BAE Systems has just signed a 42-million dollar deal with the US Ministry of Defense, to supply the US Army with a laser-based target detection system, which also works thanks to GPS technology. How target detection can be done with GPS? This system, which thanks
How to understand if a mobile phone is bugged
Bugged Mobile Phone? For those running a business where information is vital and it is also vital that the information stays confidential, the risk of being intercepted is always present. Modern technology offers a wide range of possibility to prying ears wishing to secretly listen to someone else’s conversations. How
Spying a mobile phone
Spying? If you need to be reassured on your wife’s fidelity or want to make sure that a business partner is trustworthy, you might have thought about eavesdropping their conversations; at this point the problem is, how to do it without raising any unnecessary attention. How does spying a mobile
Find your way back home safely, thanks to your cellphone
A safety application is your very best friend. If you find yourself in a city that you don’t know, you may happen to take a wrong turn and, along with losing your way, you might end up on the wrong side of town, where you could have unpleasant encounters and