Untraceable Phone? Those who, either professionally or as simple users, are involved with telecommunication security, know that encryption of telephone calls makes them more difficult to be bugged, but not impossible, especially if only one of the two users engaged in a conversation is using an encrypted mobile phone, while
Author: Michel Poe
Mobile phone bugging is now made easier
Mobile Phone Bugging? If you are using your mobile phone frequently, especially for private and confidential conversations, or if because of your work you always have the handset on to carry out negotiations or exchange information, a small piece of news which appeared on newspapers worldwide should legitimately sound as
Stealth Phone and anonymous SIM card, for an absolute privacy
Anonymous SIM card? More than once, on this blog we mentioned the Stealth Phone, that is, a mobile phone which, thanks to a piece of software discreetly installed, is capable of working on the IMEI (International Mobile Equipment Identifier) number, which unequivocally identifies each and every cellphone in the world,
Micro Earpiece: Equipment No Surveillance Agency Can Afford to Neglect
Jagson Global Network was a private detective agency run by Mr. Steve Jagson. He had a small team of eight detectives and its office located at the top floor his apartments. Jagson had over twenty years of experience in detective and surveillance activities. The agency was just four years old
An Illegal Empire Comes Down Crashing
Illegal Empire comes Crashing due to a wireless earpiece? This was going to be a never before opportunity for the City Police Department. They got an inside information that Mr. Robin Leister was hosting a big bash on his marriage anniversary; and many people wanted by police were expected to
How to turn a mobile phone into a bug
Ever heard of a mobile phone bug? One of those actions that we take automatically and without thinking, such as turning off our mobile phone, is basically just like hanging a “Do Not Disturb” sign outside a hotel door when we want to sleep a bit more, and allows us
How does a SpyPhone work?
Advanced SpyPhone software ? For those who do not happen to be experts of surveillance technology, the term spyphone may bring to their mind stories from a movie, with complicated secret agent machinery used to follow their targets basically anywhere. The truth is actually very different, as a spy cellphone,
Optical fibers to see through a wall
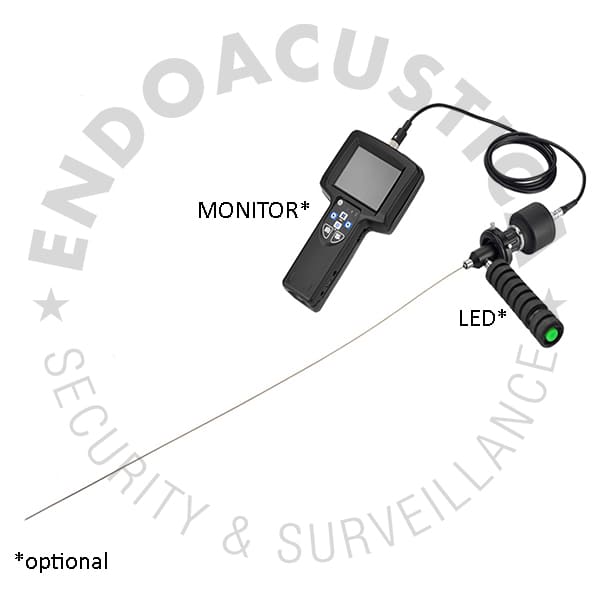
Optical fibers? Being able to see without being seen is one of mankind’s great dreams, and the principle on which our work in the information gathering and surveillance field is based; this work is of course supported by technology, and when it comes to seeing without being noticed, even a
Protection from eavesdropping
Protection from eavesdropping technology? When the information which is being circulated on our workplace is confidential, and when getting to know it might mean an advantage position and a substantial financial gain, one must make sure that all necessary measures are taken to make sure that our words are not
Micro earpieces: stay in touch at any time
In the field of surveillance and not only, using the micro earpieces can often make the difference between success and failure. A miniature earpiece, thanks to its extremely small size, can easily be placed inside the ear canal of its user, and remain unnoticed even after a thorough body check